Behind the highly-realistic fake account, called an avatar, is a security agent who can even activate the device’s camera to spy on you in real time. IMAGE/UGC
By SPECIAL CORRESPONDENT
Imagine opening Facebook to a new friend request. You click on the profile and notice mutual friends. The person shares interesting content related to your job or passion on their profile. You don’t know them, but you accept the request.
A few days later, they may send you a message or request to join a closed group you administer. They may also request your WhatsApp number to share a link concerning a cause you’re promoting online. You click the link out of curiosity.
Suddenly, without your knowledge, your device has become a virtual spy machine. Behind the highly-realistic fake account, called an avatar, is an intelligence or police agent who now has access to your personal information and can even activate the device’s camera to spy on you in real time.
Such an online sting operation might typically be used by law enforcement to track criminal gangs, hackers and terrorist outfits. But in a confidential pitch deck accessed by Forbidden Stories, these tools are marketed for potential use against journalists and activists.
Forbidden Stories found the brochure in a trove of more than 500,000 documents belonging to the Military Forces of Colombia, leaked to Forbidden Stories by a collective of hackers known as Guacamaya.
Forbidden Stories traced the brochure to a shadowy cybersecurity company called S2T Unlocking Cyberspace, with current or former offices in Singapore, Sri Lanka, the UK and Israel by matching graphics and tech descriptors on their website with those in the brochure. (S2T did not respond to requests for comment.)
The firm bills itself as an open-source intelligence (OSINT) company, yet the brochure advertises tools beyond typical OSINT, including an automated phishing tool to remotely install malware; massive advertising databases to track targets; and automated influence operations using fake accounts to trick unsuspecting targets.
The “Story Killers” project, a collaborative investigation involving over 100 journalists and 30 media organizations, started from the assassination of Indian journalist Gauri Lankesh, who wrote about the disinformation market.
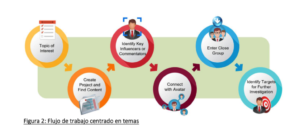
“Workflow” graphics in the leaked brochure show how S2T clients can use avatars to collect information from targets. GRAPHIC/UGC
Forbidden Stories investigated how S2T and other OSINT firms have profited from this unregulated market, pitching and selling increasingly sophisticated digital surveillance tools to clients with a track record of spying on journalists and dissidents. These firms are pitching such tools for possible use against civil society and journalists, a heightened concern in the wake of reports of abuse by OSINT firms.
“This brochure, and other publications this year about web intelligence companies, really sheds a light on a new surveillance industry that we didn’t know about that seems to be growing,” Etienne Maynier, a technologist at Amnesty International, said. “We really need to pay attention to this because there is a high risk of it being abused all around the world.”
The 93-page S2T brochure reads like a spy novel, or an episode of Black Mirror, with detailed graphics illustrating how the tool operates.
Forbidden Stories shared this document with technical experts, who agreed that the proposed capacities surpass traditional OSINT operations and can potentially be used as a powerful mass surveillance tool. “I haven’t seen such a comprehensive map tying together the whole process and so many techniques so clearly before, especially not explicitly targeting activists,” Jack Poulson, the executive director of Tech Inquiry, a US-based organization that tracks the surveillance industry, said.
“We’ve known for a long time that you have web intelligence platforms, but the narrative was that it’s a platform that’s scraping what is public and making a profile out of it,” but the difference here, Maynier, at Amnesty, said, “is that it’s actually way more intrusive.”
As the brochure describes, the OSINT system integrates facial recognition, artificial intelligence and natural language processing. The tool can, for example, use artificial intelligence to identify a face from a video, such as CCTV camera footage or videos on social media, or map the opinions or sentiments around a term or figure. Also concerning, according to Poulson, is the tool’s ability to influence the public.
In one chart, for instance, operators start from a “local political issue” and “identify key talking points and sentiment” of a target group. The talking points are then shared on social media using a network of fake accounts—or avatars—programmed to like, share and comment on each other’s posts. These avatars are hidden behind a complex web of proxies making them nearly impossible for social media platforms to detect.
For more details on this story click here.

















